Do your logs matter? Using Syslog for better logging
One of the things that can be overlooked in IT is proper logging. This is incredibly important and should not be neglected. Without proper logging in your IT environment, if you have a security incident your ability to figure out what happened could be reduced if not completely illimited. The same goes for detecting a threat on your network. IT techs love new security tools however it’s important they do not rely on said tools without building a strong foundation to prevent and detect cyber-attacks.
Out of the Box Limitations
While Windows does have logging out of the box, you’ll want to tweak these settings (usually through group policy) and consider installing Sysmon for more in-depth logging. This will help you when you need to respond to an incident or actively hunt for hackers on a corporate network. Keep in mind Sysmon is meant to complement your current Windows logging, not replace it.
Meet Sysmon
Sysmon was originally from the Sysinternals which was acquired by Microsoft. This logging solution is free from Microsoft; it complements your normal windows logs and adds in a lot of amazing information. While this is a Microsoft tool it is not installed by default in a Windows environment it is very easy to install. It can help you to detect malware and gain further insight into how things are interacting in your environment. However, to get the most out of this you should feed Sysmon logs into a proper SIEM.
Finding your blind spots
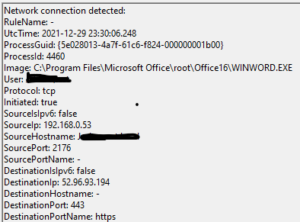
Sysmon allows you to find out where the blind spots are by providing detailed information about process creation, network connections including source process including IP address and port numbers. By collecting these logs and analyzing them you can identify malicious or anomalous activities and understand how intruders and malware operate in your network. Sysmon has its own event ID’s, notable ones:
Event ID’s
| Process creation 1 | Consumer activity 20 | File creation 11 |
| Driver loads 6 | CreateRemoteThreat 8 | Ads create 15 |
| Event filter activity 19 | Named Pipes 17/18 | File time modification 2 |
| Registry value creation or deletion 12 Modification 13 | Network connection 3 (hostname, IP, port, Process ID) | Consumer filter activity 21 |
Hashing
Another huge benefit is that Sysmon can create a hash value of all or selected binaries that run on a system. Grabbing the hash of every running process can be useful for hunting malware. Sysmon can generate your standard hashes such as MD5, SHA, and Imphash. You may be asking yourself what is Imphash?
Imphash
You know how traditional hashing works? Well, if you slightly change your file such as malware it gets a completely different hash. Attackers do this to avoid detection from standard antivirus products. Whereas Imphash hashes an executable’s function or imports of DLLs. This way you can identify related malware samples when minor changes have been made. However, Imphash will still be able to detect similar malware unless a bit more effort is put in to change the code. As we know nothing is perfect so this is should just be another cog in your defense in depth strategy.
Templates
Sysmon can be fine-tuned to your environment for log collection. It uses an xml configuration file. A good starting point is Swift on Security’s template. You can find it Here.
Installation
To directly download Sysmon from Microsoft click below.
Direct Microsoft download. You then will need to install it from the command line with administrative rights.
Example: sysmon.exe -accepteula -i sysmonconfig-export.xml
RT Solutions has provided a PowerShell script here to download and install Sysmon with Swifts on Security’s template. This script was updated in 2023 to include the ability to update Sysmon to the latest version.
Where to find Syslog logs
Logs can be found under: “Applications and Services Logs/Microsoft/Windows/Sysmon/Operational”
Summary
Your logs matter. Sysmon is great and you should consider using it if you aren’t already. It’s better to be prepared than not when the SHTF.