Blog

That long password isn’t keeping you better protected
Even passwords of 15 characters can be cracked by cyber criminals. Our latest tech update explains what to do instead

Get ready for another game-changer from Teams
Microsoft is working hard to lead the AI revolution and its latest update to Teams will certainly make it a front-runner. We think the potential is unlimited, here we’ll tell you why.

Are you ready for Windows 11 to get even better?
Windows 11 has already boosted our productivity and saved us time, but it hasn’t finished improving our working lives just yet. We have all the details.

That phishing site? Gone in 600 seconds
This latest stat we learned about phishing websites really surprised us. And it comes with good news about an enhanced way to protect your business. We give you all the details
Microsoft 365 you’re already paying for but might not be using.
Unlock the Hidden Potential of Microsoft 365: 10 Productivity Apps You Already Have, but May Not Be Maximizing Microsoft 365 isn't just Word, Excel, PowerPoint, and Teams; it's a powerful platform built to supercharge...

Beware these “too good to be true” Facebook ads
Facebook can be a great platform to advertise your business but criminals have a new scam that you need to be aware of. We tell you what to look out for.

And breathe… the “file too large to send” problem is over
Microsoft finally has a fix for one of the oldest and most frustrating problems in Outlook – when the file you’re trying to send is too big. Here’s what’s changing in the next few weeks and how it affects you.

Microsoft and Samsung team up to boost work phone security
Microsoft and Samsung have joined forces to keep the data on your work mobiles safe and secure. We give you all the details

Is that Microsoft email actually a phishing attack?
Which company has become the #1 most imitated in phishing scams? We’ll tell you more…

Google Calendar has a great update for hybrid workers
Want your team to know where you are when you’re not in the office? We explain how Google Calendar’s new feature lets you share multiple work locations each day.

3 ways AI makes almost any business task easier
AI tools like ChatGPT and Google’s Bard can help you boost productivity and actively grow your business. How? We have the details.

The hidden dangers of free VPNs: Are you at risk?
Free VPNs may seem tempting, but they could be exposing your data to cyber criminals. We tell you how to protect your business.

Is this the ultimate browser for business?
There’s a new browser that keeps work and personal browsing totally separate. Here’s how it works and when it launches.

Defending Against Human Error: The Critical Need for Cyber Security Awareness Training
Small and medium-sized businesses are highly vulnerable to cyber attacks, with their employees being the weakest point of entry. To protect your business, it's crucial to provide comprehensive cybersecurity awareness training...
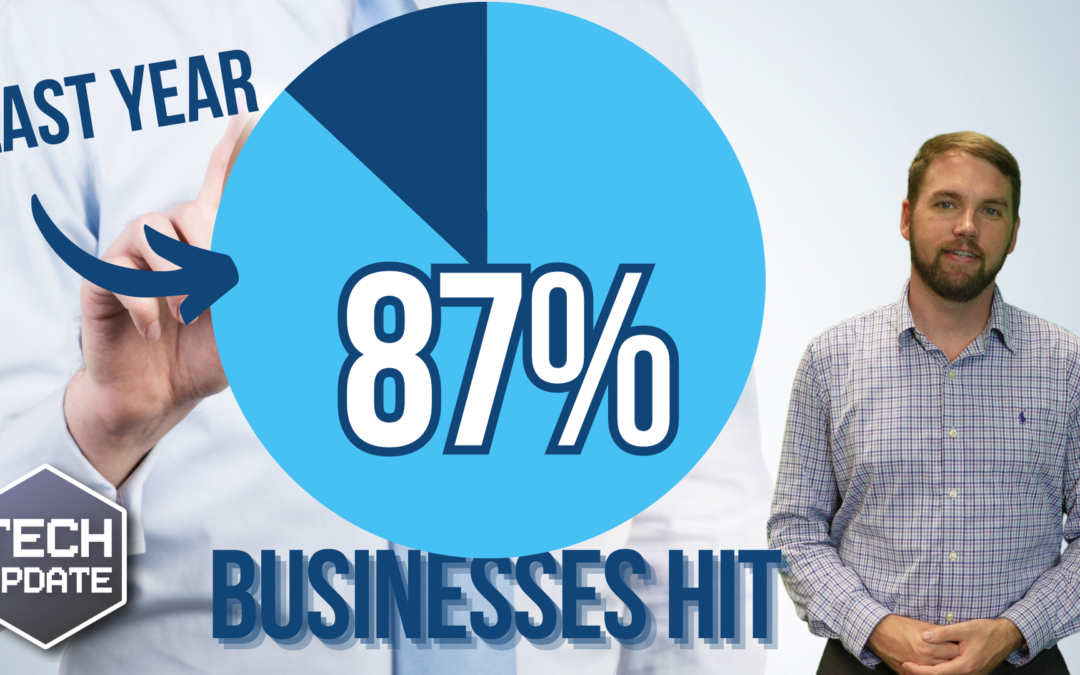
Scary stat: 87% of businesses hit by this in the last year
Cyber attacks aren’t reserved for big corporations. We show you how to protect your business from cyber criminals

Prepare for the Inevitable: Safeguard Your Business Against Ransomware Attacks
Ransomware is a major data security threat for your business, and it's truly frightening. Imagine your staff logging in one morning to find a bright red screen, revealing that your data has been locked and a massive Bitcoin...

This is the latest trend in phishing attacks
Cyber criminals are using images embedded into emails.
We’ll tell you how to protect your business from these new phishing scams.

The Essential Guide to Setting Up the Perfect Video Setup on Any Budget
Have you ever been on a video call where the other person looked and sounded terrible? Maybe they were looking down at their laptop webcam, which isn't the best angle. They were poorly lit, making them look suspicious, and their...

Browse with confidence: Microsoft Edge’s security boost
We explain how Microsoft Edge is introducing some new security-boosting features to help you stay one step ahead.
Now AI can make your Teams meetings more productive
Microsoft Teams Meeting Recap will summarize your meetings and even make a list of the action points. We show you its other benefits
